Almost everyone knows and uses the Internet but almost nobody knows about its most modern and secure architecture- it's called SCION (SCALABILITY, CONTROL, AND ISOLATION ON NEXT-GENERATION NETWORKS). Read this blog article to learn more about it and how it compares to traditional internet architecture.
Traditional Internet architecture overview
The Internet is a world-wide global system of interconnected computer networks. Using the Internet, we can share data and information across the globe instantly. The Internet has made the world a smaller place to live in. We rely on constant Internet access via our mobile phones, laptops, PCs, IoT devices, home automation devices, etc. for communicating with others, shopping, digital banking, social media, work and so much more it's hard to even list all of its uses.
Nowadays most people find it hard to live without the Internet. From an architectural perspective the Internet is just an interconnection of multiple networks or “networks of networks”. It's the connection of computer networks around the world into one entity, so to speak. It's not one big computer, but rather numerous computers and devices connected together. The Internet has become so big it's impossible to capture it on one screenshot however there are websites providing interactive Internet maps .
Another approach is to visualize the Internet as a galaxy of websites/web services available a good visualization has been presented below:
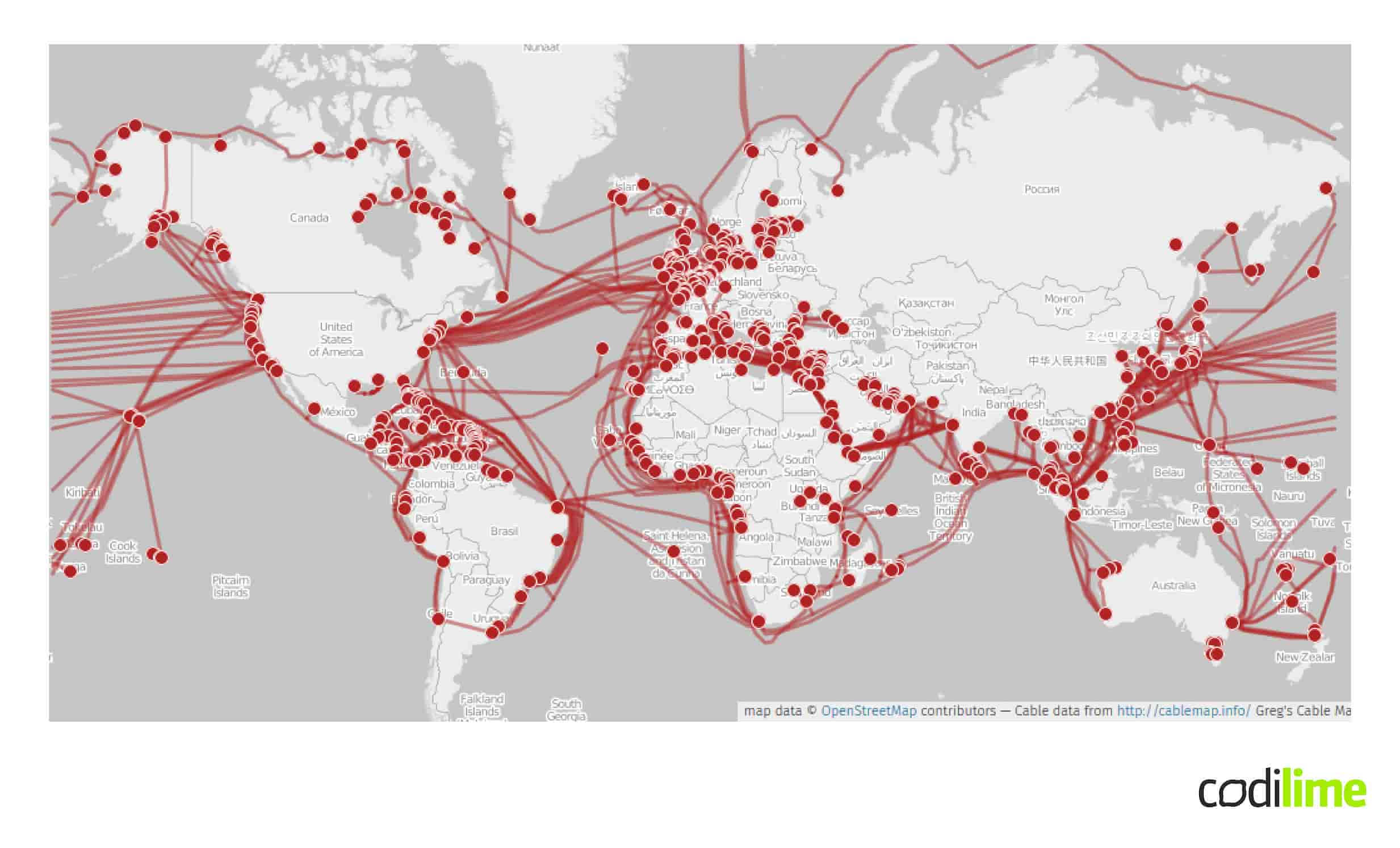
To be able to interconnect all continents a very sophisticated physical undersea network has been built around the world which has been shown below:
So, as we now have a grasp on what the Internet is, let’s answer the question of how it got started?
The history of the Internet
Before the Internet era computers were just one big mainframe without the ability to “talk” with any other computer. There was no technology nor terminology to put two computers and connect them via any kind of “network”.
Historically the origins of the Internet started in the 1960s when the U.S. Advanced Research Projects Agency Network (ARPANET) started to develop its public packet-switched network.
The first successful message between two computers happened on 29th of October 1969 when Charley Kline - a student at the University of California Los Angeles (UCLA), tried to log in to the mainframe at the Stanford Research Institute (SRI ).
The first command sent to the remote terminal was “LOGIN” - it required two attempts as the first attempt crashed after Charley typed “LOG” but they managed to fix the problem and successfully logged in to the remote terminal at SRI on the second attempt. Initially ARPANET was an exclusive club of interconnected US universities and government facilities (e.g. Department of Defence) but it started to grow and grow over the years and more and more organizations have been connected to it, including on other continents (via satellite links).
However because different networks that were connected to ARPANET were using different network protocols some networks could not talk to each other. To overcome that challenge the TCP/IP protocol stack was developed in the 1970s resulting in the first initial TCP RFC draft in 1974 - RFC675 .
The term “Internet” was first used in that RFC as a shorthand for internetwork. It took almost 10 years to make the TCP/IP stack the ARPANET standard and all of its nodes were migrated to TCP/IP stack in 1983. Other, older protocols like the Network Control Program (NCP) developed in the 1960s were deprecated. Telnet and FTP (File Transfer Protocol) emerged as the first applications utilizing the Internet network (available since 1969).
The ARPANET was shut down in 1989 (and finally decommissioned in 1990) in favor of The National Science Foundation Network (NSF) which practically replaced the backbone of the Internet. In 1986 NSF built a 1.5 megabit/second network which became known as NSFNET. Many commercial and other ISPs (internet service providers) were introduced during that time and connected to that network.
Although the Internet has grown significantly since 1974 other factors have greatly contributed to make that growth even bigger, including ethernet standards, commercial routers/switches from Cisco/Juniper companies, LAN networks using ethernet standards, and mature implementations of TCP/IP on Unix and Linux systems.
Before 1991, the Internet was mostly used by scientists and government agencies to exchange information and data. In 1991, the World Wide Web (WWW) was introduced. Although the initial growth of the internet network was begun in the United States, it was the CERN project which initiated massive growth of the Internet by introducing the initial WWW and HTTP standards which make the Internet easier to use for regular users rather than just scientists and governments. To learn more about HTTP protocols you can read this article.
Currently, according to IXPO organization:
- The indexed web contains 2.25 billion pages
.
- 4.95 billion people
used the internet in January 2022 (62.5% of the world’s population).
- According to Statista, in 2025, we will send over 376 billion emails
daily.
- IDC estimates that the global datasphere will grow to 175 zettabytes by 2025
(1 ZB equals 1 trillion GB).
- IOT Analytics reports that 27.1 billion Internet of Things devices
will exist by 2025.
A brief history of the Internet
Below you can see a visualization of the major Internet milestones:

To sum it all up, the history of the Internet is important, vivid and dynamic. However, during its development, some aspects of modern internet usage were not anticipated. These will be discussed in the sections below.
Modern Internet architecture
So far, we have focused mostly on a general overview of the Internet and its history. This chapter will describe how modern Internet architecture works and what its drawbacks are.
In general, the existing Internet architecture consists of three tiers of ISPs (internet service providers):
Tier 1 networks
Exchanges Internet traffic with other Tier 1 providers on a non-commercial basis via private settlement-free peering interconnections. Essentially this is the backbone of the current Internet network. They will also interconnect at internet exchange points (IXPs). Tier 1 ISPs can deliver the best network throughput over the Internet backbone through these private peering connections because they own their network infrastructure and have direct control over how traffic flows through these connections. But they are expensive and there are dozens of them as they have to span continents - the full list can be found at: Tier 1 Networks List
Tier 2 networks
Service providers that utilize a combination of paid transit via Tier 1 ISPs and peering with other Tier 2 ISPs to deliver Internet traffic to end customers through Tier 3 ISPs. Tier 2 ISPs are typically regional or national providers.
Tier 3 networks
Service providers that purchase Internet transit. A Tier 3 provider is by definition primarily engaged in delivering Internet access to end customers. Tier 3 ISPs focus on local business and consumer market conditions. Their coverage is limited to specific countries or sub-regions, such as a metropolitan area. Tier 3 ISPs utilize and pay higher-tier ISPs for access to the rest of the Internet.
The below image illustrates the relationship between the different tiers and end-users:

How do ISPs exchange routing information?
So the key to gaining Internet access is to connect to an internet service provider - the question is how can ISPs trust each other and exchange routing information?
For that purpose, the BGP (Border Gateway Protocol) is used which allows the exchange of IPv4 and IPv6 prefixes between ISPs. The global Internet is a collection of separate, but interconnected networks, each of which is managed as a single administrative domain called an autonomous system (AS). There are over sixty thousand AS numbers (ASNs) assigned to a wide variety of companies, educational, nonprofit and government entities.
The AS networks that form the primary transport for the Internet are independently controlled by internet service providers (ISPs), each with its own business policies, internal network topologies, services, and customer profiles. The binding glue of the Internet is that all ASs share a standard Internet protocol (IP) addressing scheme and global Border Gateway Protocol (BGP) routing framework that allows all these networks to interconnect with each other directly or indirectly.
However, it is hard to establish clear and open relationships for ISP BGP route exchange policies and this can lead to many misunderstandings or even BGP-based prefix hijacking, which happens multiple times every day and affects even biggest companies like Microsoft, AWS, Google, Apple, and Mastercard- for more details you can read these articles .
That's the major concern regarding traditional Internet architecture - it was not built to prevent such issues and a more modern approach has arised called SCION - so let's talk about that.
SCION Internet architecture
SCION (Scalability, Control, and Isolation On Next-Generation Networks) is a completely different approach to global Internet architecture - it focuses mostly on security, control, robustness, high availability and isolation. It is considered by IETF to be a “future Internet proposal” based on new path-aware networking.
Unlike traditional internet routing protocols that rely on fixed routing tables and hop-by-hop forwarding, SCION offers more flexibility and control over traffic routing through advanced features such as path-aware networking and policy-based routing (PBR) equivalent.
SCION is a path-aware protocol and as such aims to replace the BGP protocol widely used in the Internet. Path-aware architecture allows end hosts (or gateways) to learn about available network path segments and combine them into end-to-end paths that are carried in packet headers.
Benefits of SCION
The most important benefits of SCION in comparison to traditional Internet are:
- Highly available communication - multipath communication is used and enabled by default. It provides immunity to current BGP-level attacks, such as prefix hijacking.
- Client path control, for example for compliance purposes. SCION can guarantee the path each packet takes; in particular, which ISPs or geo-locations are NOT traversed.
- Secret paths - can only be used by selected communication partners. Cryptographic path protection enables path hiding even if an attacker knows the network topology, thus making the path impossible to DDoS.
- VPN link protection - a VPN link can be provided by the SCION network, providing all the properties listed above for the end-to-end VPN tunnel.
- Faster path failover.
- Interoperability with existing network infrastructure - SCION can be used on top of existing IP networks - in this scenario a SCION-IP gateway (SIG) can be used in order to encapsulate SCION headers on top of a TCP/IP stack - in this scenario SCION is less efficient as it is not end-to-end but you can leverage existing IP networks to transport and tunnel SCION-enabled traffic and still access a lot of SCION’s benefits, especially with regards to security. To extend SCION-aware networks, SCION border routers (BRs) can be deployed within an AS to support native SCION-enabled communication.
- Transport agnostic - SCION can run natively (just using SCION headers) or use any commonly-used underlay transport regardless of whether it is an IP network, MPLS network, etc.
- BGP-free - the BGP protocol is no longer required to advertise the available paths that are resilient to any BGP-related attacks, vulnerabilities. SCION is meant to replace BGP in the Internet.
- Data plane processing reduction - less processing on packets.
By its very nature, SCiON offers three unique properties critical for business communication in the form of control, reliability and security:
The whole project started in 2010 at ETH university in Zurich, Switzerland. SCION implementation is open source - below you can find a few handy resources:
- Source code
of SCION project.
- ScionArchitecture.net
- Books, papers, videos, tutorials, etc. for educational purposes.
- Anapaya documentation
of SCION production network including protocol headers, cryptography, tools, etc.
- Anapaya
- Production SCION network project where enterprise entities can arrange to be connected to the global production SCION network.
- SCIONLab.org
- a global research network to test the SCION next-generation Internet architecture. Anyone can join the research network if they meet some basic requirements, like having a public IP, etc. This helps organizations to understand the capabilities and power of SCION architecture.
Types of SCION networks
There are two types of global SCION networks deployed currently:
-
Research Global SCION Network - SCIONLab - used for education, test and research purposes for SCION:
- Anyone can participate in it and create up to five SCION-enabled ASs connected to the global research network.
- Infrastructure of SCIONLab comprises a network of globally connected ASs and ISDs (isolation domains).
- Minimal requirements - mainly Internet public IP and being able to communicate via UDP ports inbound and outbound.
- Easy to set up - all required components can be deployed as a set of VMs, installed as packages, or can be build from the source code.
SCION also has some limitations compared with a production network:
- PKI control plane is centralized as opposed to real production deployment, meaning a single point of failure but it does make key distribution easier and faster which is more important for educational purposes.
- Overlay links (over public Internet) are used for both within the infrastructure and between the infrastructures of user ASs - reducing capabilities in terms of security, availability and performance of full SCION deployment but also reduces complexity.
The below image shows the topology of the current global SCIONLab network:

- Production Global SCION Network - Anapaya (spin-off company of ETH university) production-grade global SCION network - at the time of writing, mostly used by Swiss banks and financial institutions but more and more ISPs and enterprise entities are joining - the current SCION-Internet (ISPs) map is below:
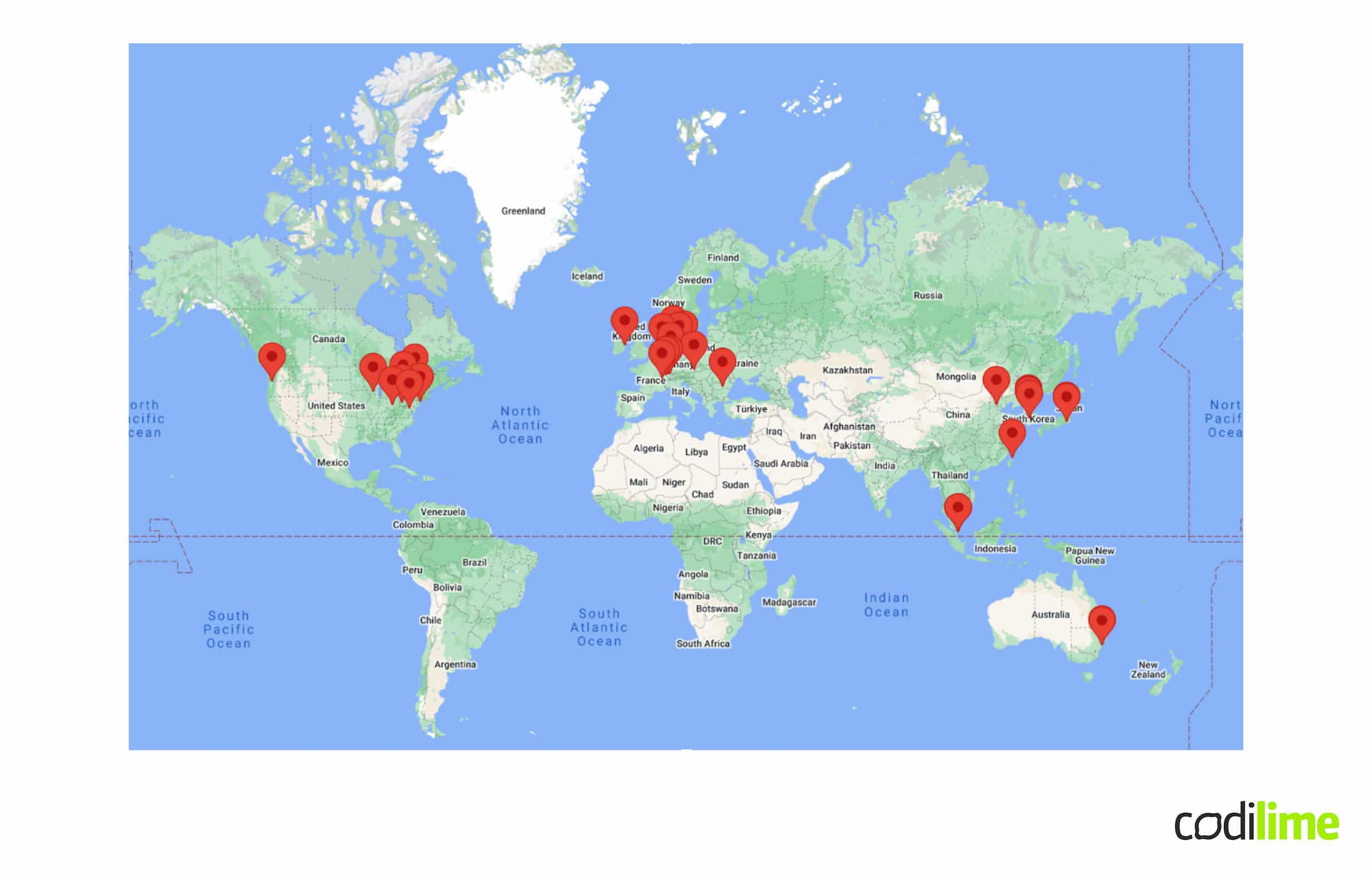
If an enterprise joins the Production SCION-Internet it can utilize the full potential of the SCION protocol - including but not limited to:
-
Control:
- Policy-based path selection - gives control over the traffic flow to be prioritized based on location, speed, cost, quality, latency, jitter, or even CO2 emissions.
- Geofencing - Certain paths can be avoided or discouraged - e.g. countries, jurisdictions, regions, etc.
-
Reliability:
- Multipathing - based on the path selection policy, multiple paths can be used in order to reach a destination - this ensures no downtime and compliance with your path-selection policy (for instance, a preference for speed).
- Fast fail-over - as SCION has access to multiple paths failure of one of them result in sub-second failover to another path in case of one path failure.
-
Security:
- Immune to routing attacks - BGP is not used in SCION, a path-aware protocol with cryptography in mind - everything is based on routing policies.
- Immune to prefix-hijacking.
- PKI built-in to secure control plane communication.
Components of SCION Internet architecture
SCION architecture has been built with security, scalability, control, isolation and multipath paradigms in mind as opposed to the traditional Internet.
The main components of SCION architecture are:
- Isolation domains (ISDs) - entities which are nothing more than logical groups of ASs (autonomous systems) - an independent common jurisdiction and failure domain.
- ISD core - ASs that manage the core of the SCION network, providing global connectivity - responsible for policy within ISD domains.
- Core AS - AS which is part of the ISD core.
- Routing - can be separated into inter-ISD and intra-ISD domains, which is similar to OSPF/IS-IS Areas/Levels - separation of control plane.
- Trust root configuration (TRC) - negotiated by the ISD core within ISD - every ISD has its own trust roots - it resolves issues of oligopoly models (Web PKI) and monopoly models (DNSSEC, RPKI) and also ensures that external attacks are almost impossible against internal ISD routing policy.
- Intra-ISD beaconing system - to advertise possible paths within ISD, traversing all ASs within the ISD to provide multipaths via the ISD core.
- Inter-ISD communication - if host ‘S’ wants to communicate with host ‘E’ in a SCION network, there are three ISDs (blue, orange and green) - the below graph illustrates the process:

Below an overview of a simple SCION topology illustrates the concepts and components:

SCION routing process
In terms of the routing process, SCION uses something called “Beaconing” instead of BGP - full documentation about the process can be found in this article. In a nutshell, Beaconing process is responsible for advertising ( path registration of) new paths and for existing path discovery (the path exploration process).
See the below table for a comparison with traditional BGP:

If you want to know more planes in networking, read the article “Management vs. Control vs. Data Planes in a Network Device”.
The BGP protocol has an optional multipath capability which can be used however it is not enabled by default and it requires additional configuration - also each vendor can vary their specific implementation. It is not widely used in Internet implementations.
With regards to the SCION protocol as such, full documentation can be found here. It can be ‘tunneled’ over existing TCP/IP networks but an additional 80 bytes is needed to transport the additional SCION information, or it can run natively.
Below is a sample topology showing how SCION can be tunneled over IP networks:

With regards to the protocol itself it introduces a couple of new headers:
Common header - shared across all SCION traffic:
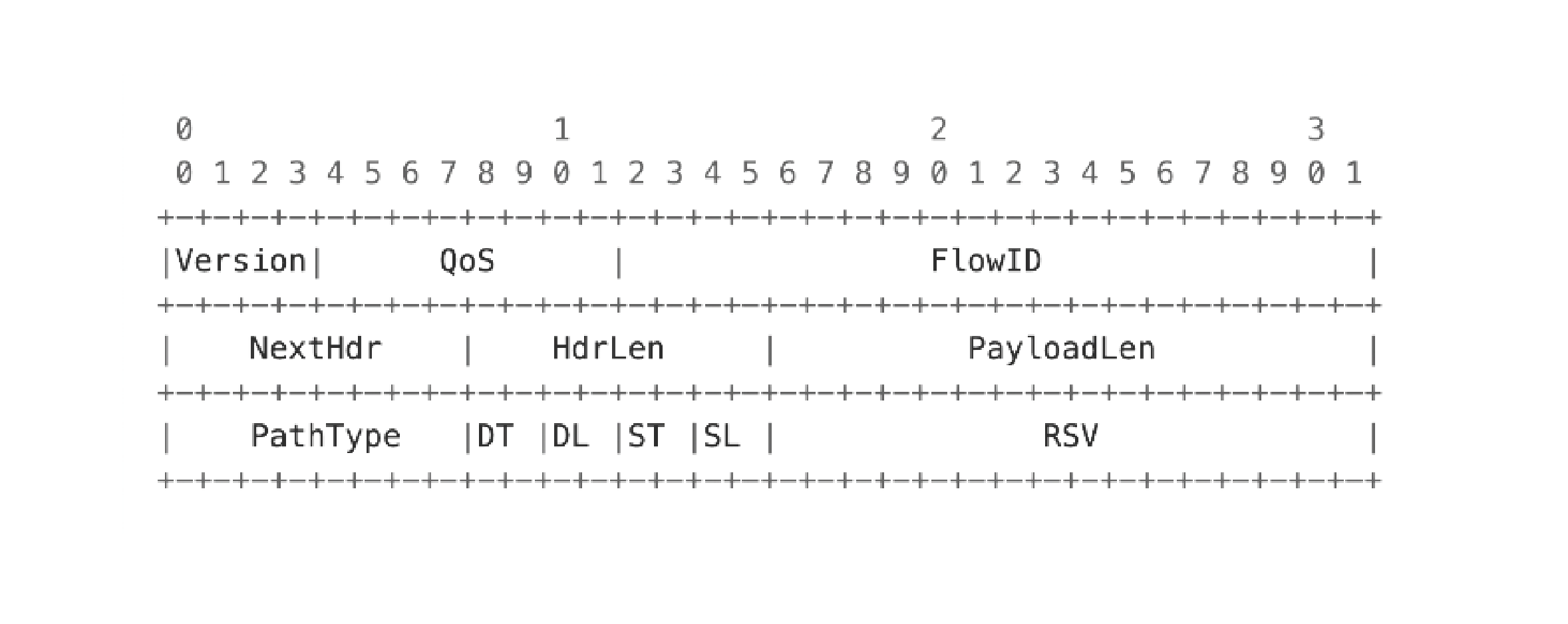
Address header - to identify the source and destination of traffic - identifies ISD, AS and host addresses:

Path type header - information about path metadata, hops (up to 64) and additional information (optional):
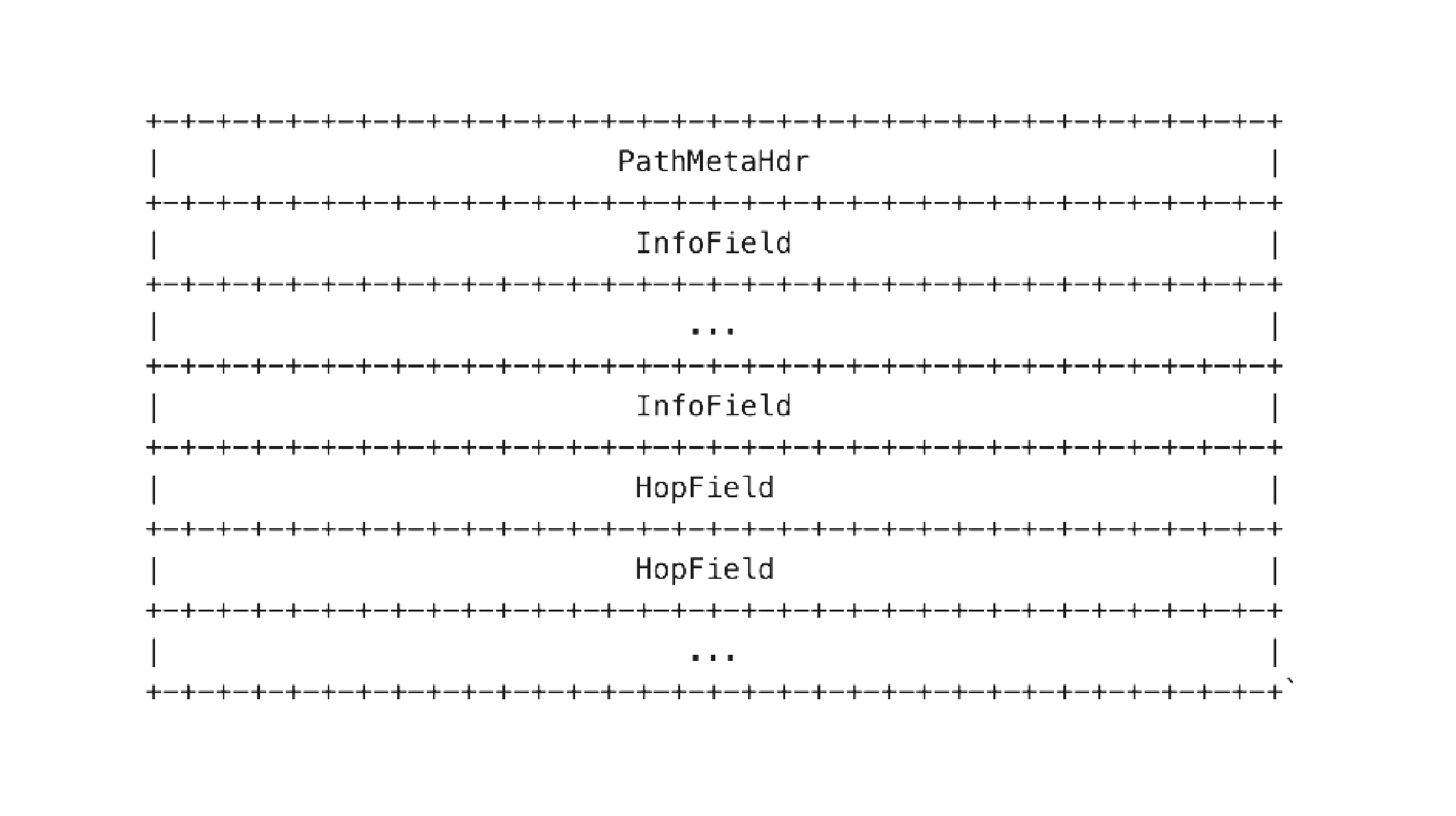
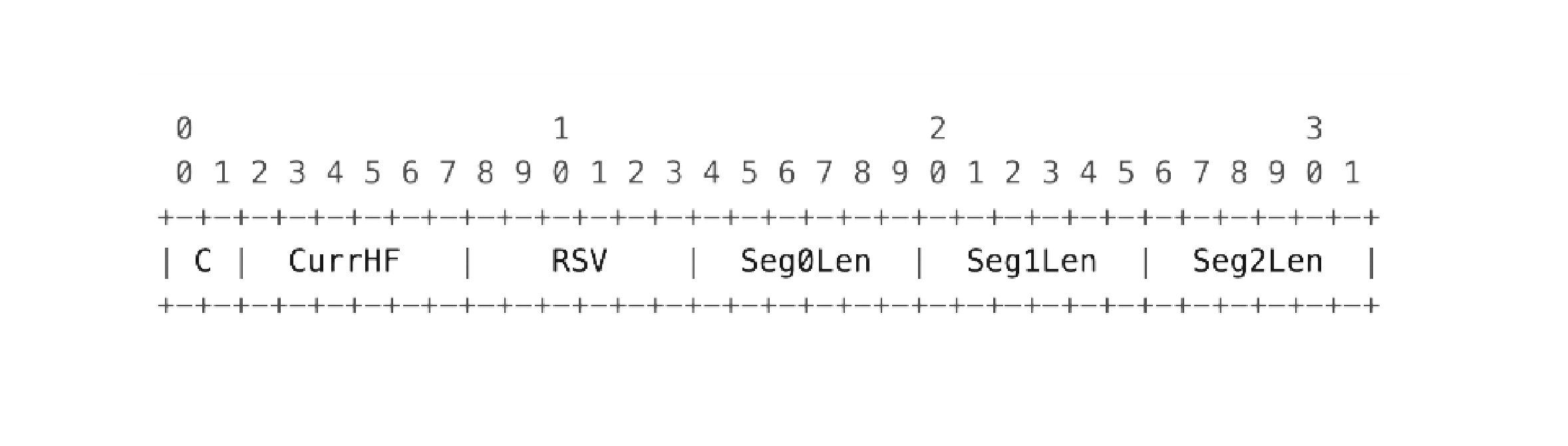
PathMeta header - carries metadata information for a specific path header:
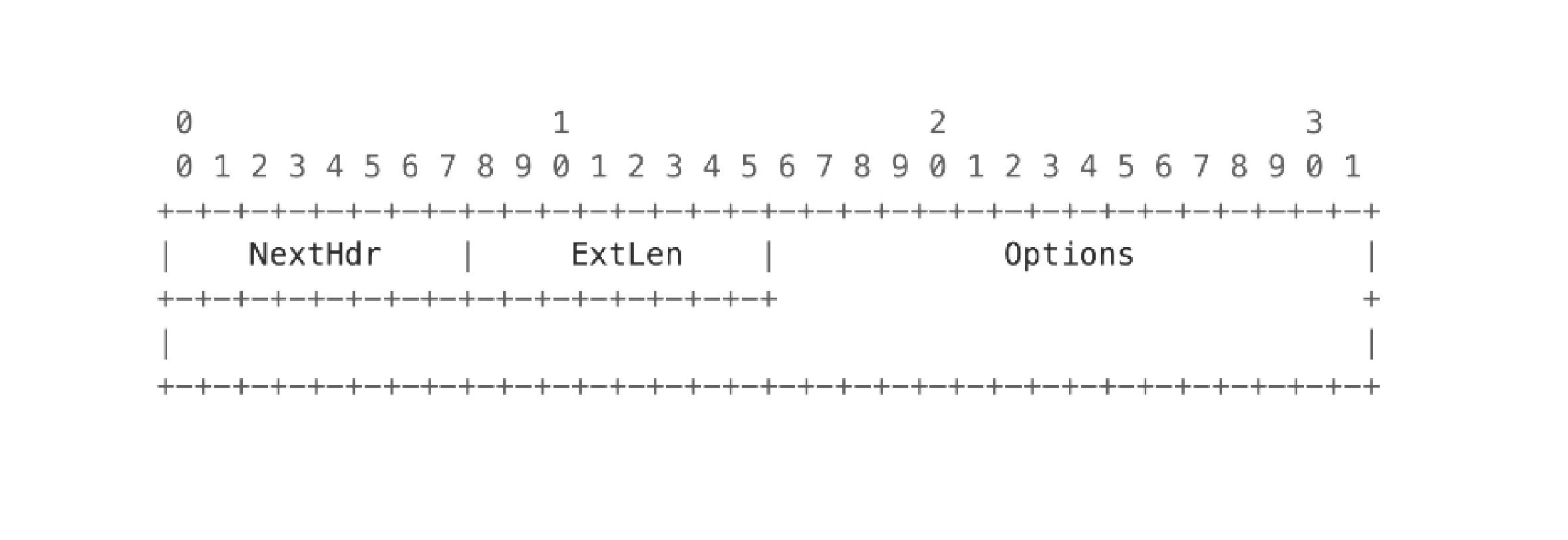
Extension header - any future extensions to the SCION protocol are implemented with the below format:
SCION - Summary
As with any protocol, SCION does have its drawbacks - the main potential issues are:
-
Additional latency to obtain paths:
- This can be avoided with caching & path reuse - due to paths in the packets - similar to the DNS process.
-
Bandwidth overhead - new information is required in protocol headers so more space is used in the packet:
- No space is wasted as all information is used and it provides path control, simpler data plane, etc.
-
New certificates might be needed (e.g. for TRC certs):
- Benefit is higher security.
-
Learning curve:
- Engineers must learn the new protocol and approaches.
However, the benefits outweigh these drawbacks as the new protocol offers a whole new approach to Internet traffic, as outlined in this article - especially in terms of routing control, security, scalability and high availability. It gives full control over the routing process to end-systems - you can decide on the best path for your traffic, where “ best path” could mean: fastest, most inexpensive, avoiding certain regions or jurisdictions, or lowest CO2 emissions.
Additionally, as SCION integrates the full PKI infrastructure, and each packet is signed and verified, it provides additional security and last but not least, it is BGP-free, using a new approach to routing called beaconing.
Also it is easy to test the SCION infrastructure using the Research SCION network where anyone can participate.
Below you will find a list of additional resources (in addition to those listed in the article itself) if you would like to learn more about SCION:








