In a high-pressure environment like a Security Operations Center (SOC), where thousands of alerts can appear every hour, security teams can easily feel overwhelmed, and risk missing critical steps. Imagine trying to handle 15,000 alerts per hour, many of which are false positives. This is the reality for SOC teams, which can be quickly overburdened, losing focus and slowing down their responses to real threats.
To manage this, a well-organized framework with clearly defined roles, skilled specialists, and the right tools is essential. This is the essence of a SOC: a dedicated team where people, processes, and technology collaborate to prevent potential security breaches and detect, assess, and respond to threats efficiently, minimizing risks and ensuring consistent, effective, and timely responses during a crisis.
Among these essential SOC tools, SIEM and SOAR stand out as foundational. In this article, we will explore their primary functions, compare these solutions, and discuss how to choose the most suitable tool for your organization.
What is a SIEM?
A SIEM (Security Information and Event Management) platform collects, aggregates, and analyzes log data across an organization’s infrastructure to identify suspicious activity. By centralizing data from various sources, SIEM provides real-time alerts, event correlation, and the ability to review historical data for incident investigation. This enables SOC teams to monitor their environment comprehensively, detect potential threats, and gain insights to strengthen their security posture.
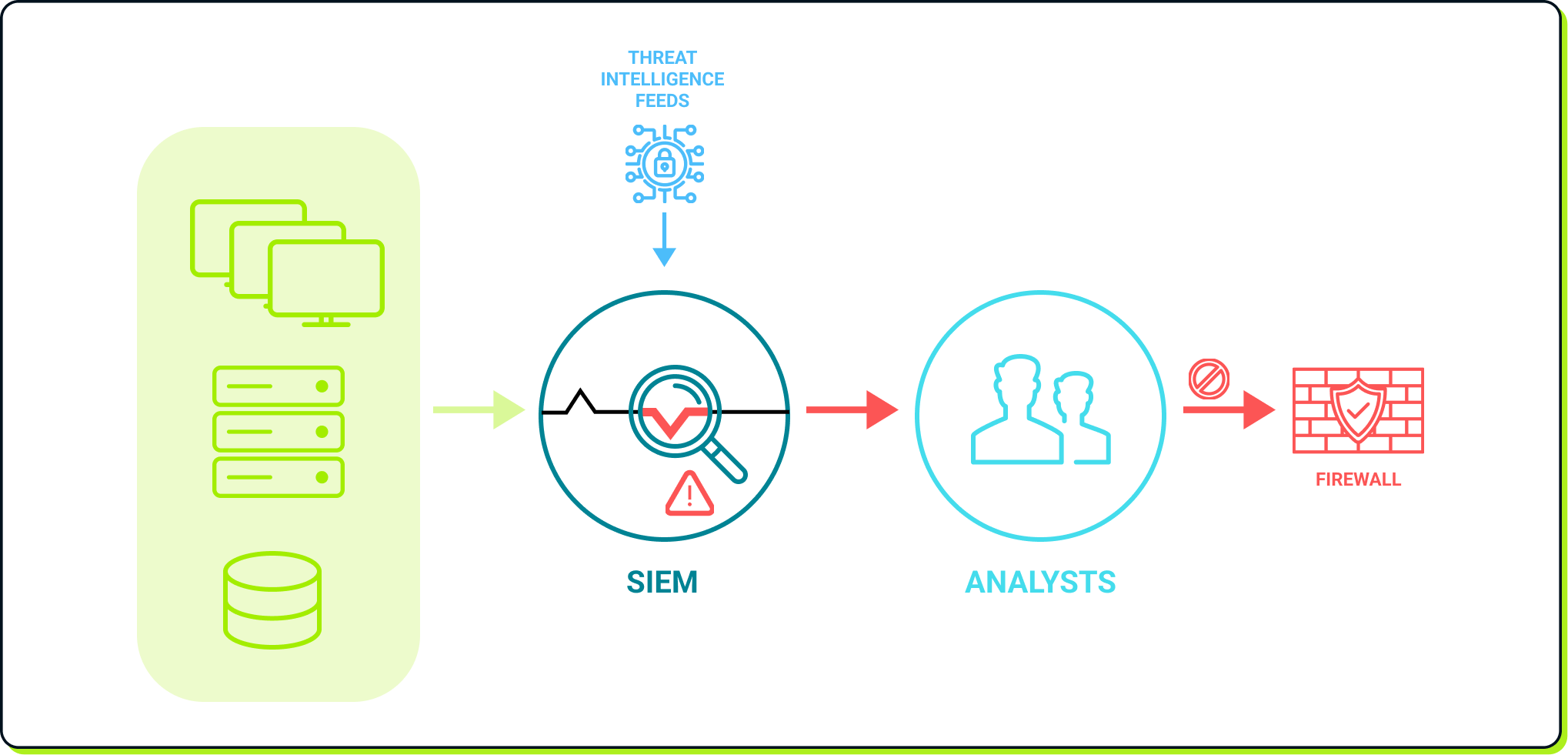
SIEM in action
Using the image above as an example, various devices, such as workstations, servers, databases, and other network equipment, send logs to the SIEM. The SIEM stores and analyzes this data based on predefined rules, historical analysis using AI models, and information about known malicious actors from Threat Intelligence sources. If a suspicious pattern is detected as a potential incident, analysts are alerted. After investigating, they assess whether it is a true positive alert and determine the appropriate actions to mitigate the threat, such as adding a block rule to the firewall.
As we can see, a SIEM serves as an analytical platform. While it does offer response capabilities, these are typically limited to basic actions and scripts. Analysts are still responsible for manually triaging alerts and carrying out the full incident response workflow, such as creating firewall rules to block suspicious network connections. In essence, a SIEM provides the intelligence but lacks the operational execution.
SIEMs can also send alert notifications to other platforms, like SOARs, to carry out automatic actions.
A Typical SIEM Use Case
Let’s consider a typical SIEM use case involving a sophisticated phishing attack that compromises a user’s account and ultimately leads to the exfiltration of sensitive data. Without a SIEM in place, an analyst might only learn about the incident after it has already progressed significantly. Perhaps when a media outlet reports a data leak, when the user realizes they have been a victim, or when a security device such as a firewall or IDS/IPS issues a vague alert about unusual connections or unexpectedly large data transfers.
Once the analyst finds out about the breach, the investigation would demand pulling logs from multiple, separate sources: email server logs to determine when and how the phishing message reached the user, authentication logs to identify suspicious login patterns, and network flow records to understand the path of the anomalous data transfers. The analyst would piece together a timeline, verifying each step of the attacker’s actions one log at a time, potentially missing subtle correlations and indicators along the way.
With a SIEM in place, the situation unfolds very differently. A SIEM continuously collects and normalizes logs from across the environment, making it possible to search and analyze all event data from a central console. As soon as the victim receives the phishing email from a suspicious address, the SIEM’s alerting capabilities flag this activity. If the user then executed a file that opened a remote C2 (Command & Control) connection to a known malicious host, previously identified in the SIEM’s integrated threat intelligence feeds, the SIEM would immediately raise the severity of the alert, recognizing it as part of a likely command-and-control infrastructure.
Later, when the attacker attempts to move large volumes of sensitive data out of the network, the SIEM’s behavior models would detect that this transfer was unusual for that user and report it as suspicious. At each step, the SIEM would enrich and correlate events, quickly linking the initial phishing email to the established C2 channel and the subsequent data exfiltration. This correlation happens in near real-time and from a single interface, enabling analysts to understand the full scope of the incident rapidly.
Most importantly, whether discovered at the first phishing attempt or during the later data exfiltration stage, the SIEM allows analysts to efficiently trace the attacker’s entire sequence of actions. The SIEM aggregates all related events in a clear, easily navigable format, making it far simpler to identify how the attacker entered the environment, which vulnerabilities were exploited, and which assets were compromised. This visibility empowers analysts to swiftly contain the threat, remove the attacker’s foothold, address security weaknesses, and reduce the likelihood of similar incidents in the future.
What is a SOAR?
A SOAR (Security Orchestration, Automation, and Response) platform helps SOC teams respond quickly to incidents by automating repetitive tasks and coordinating workflows between security tools. Using predefined playbooks, SOAR platforms can automatically carry out response actions, reducing the time and manual effort required for incident response. This helps SOC teams handle incidents faster, more consistently, and with a lighter manual workload.
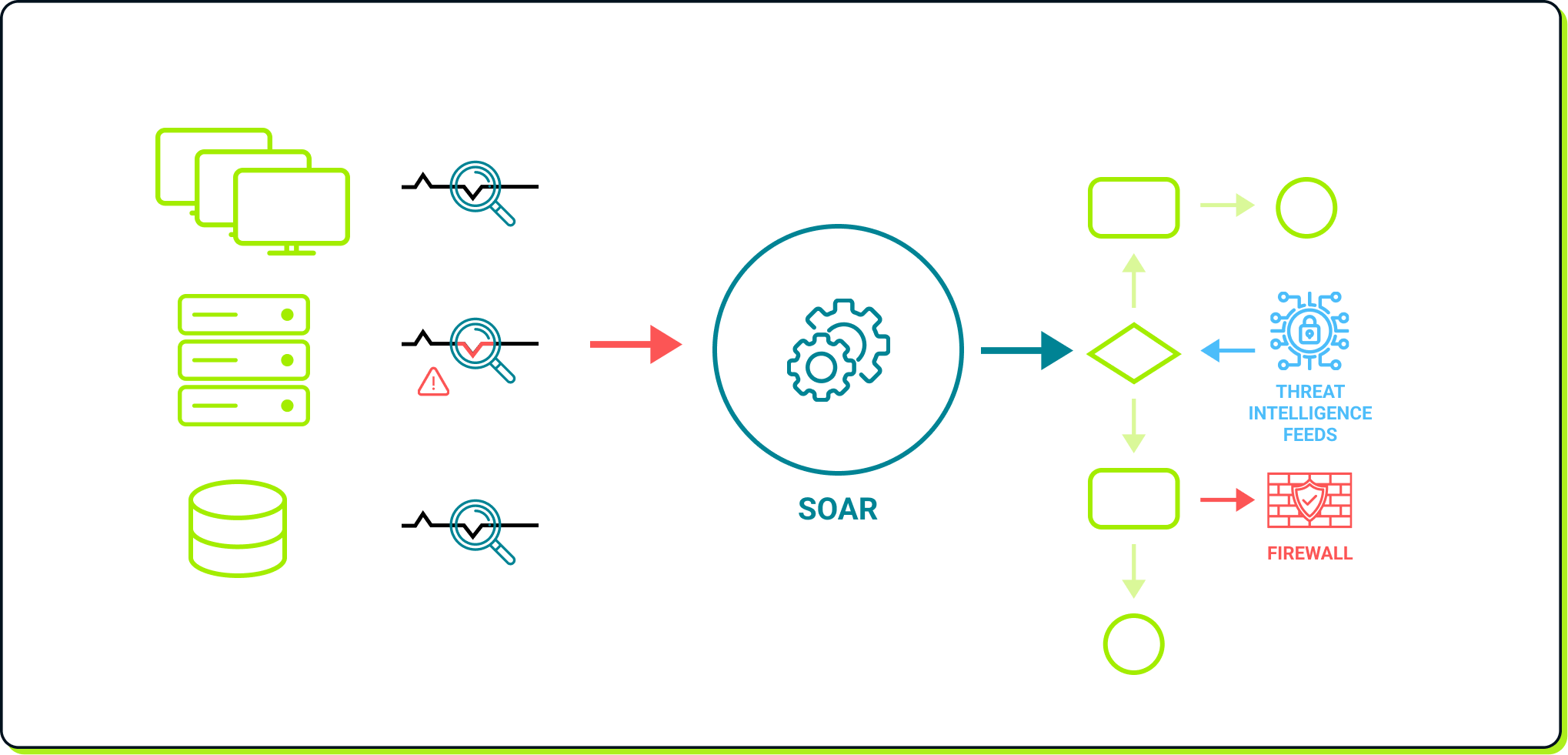
SOAR in action
In the image above, detection engines analyze endpoints and databases, sending alerts to the SOAR when threats are detected. The SOAR then executes a playbook to triage the alert and confirm whether it's a true positive. If confirmed, the SOAR follows the most appropriate course of action, such as, in this case, adding a firewall rule to block the network connection.
As illustrated, SOAR platforms generally do not perform direct threat detection. Instead, they rely on inputs from other tools such as EDRs, antiviruses, IDS/IPSs, and even SIEMs! Upon receiving these detections, a SOAR automates alert triage using advanced playbooks, identifies appropriate actions, and executes them across various platforms in the network.
In a few cases, manual intervention is only needed to approve or reject the suggested actions, drastically reducing the time spent on repetitive tasks and enabling teams to focus on higher-priority issues. Unlike SIEMs, SOARs lack analytical tools, but they excel in the automation of complex tasks and operational execution.
A typical SOAR Use Case
Let’s revisit the phishing attack scenario. Without a SOAR, once the phishing alert is received, the analyst must manually investigate and respond to every aspect of the incident. They would begin by confirming the threat, cross-referencing indicators, like the sender’s address or the URL in the email, with threat intelligence sources, and analyzing the downloaded file. If the email is deemed malicious, the analyst would then move to take action: they would log into the identity management system to disable the compromised user’s account, access the firewall or network security tools to block the IP and domains associated with the attacker’s command-and-control (C&C) infrastructure, and work with endpoint security tools to isolate the infected machine.
Each of these steps would require the analyst to switch between multiple tools and platforms, manually performing repetitive tasks and documenting their actions along the way. Forensic evidence, such as logs or file hashes, would have to be collected manually from disparate systems for later analysis, and communicating with affected stakeholders would rely on the analyst drafting emails or opening tickets in the organization’s IT service management platform. The entire process is slow, fragmented, and prone to errors that could give the attacker more time to escalate their actions.
With a SOAR, the process would look entirely different. As soon as the phishing alert is triggered, the SOAR automatically executes a predefined playbook for phishing incidents. It would validate the threat by cross-referencing the email’s indicators against integrated threat intelligence feeds. Once confirmed as malicious, the SOAR would proceed to disable the compromised account by connecting directly to the identity management system. At the same time, it would communicate with the firewall to block the attacker’s IP and domains, severing the C&C channel, and instruct the EDR system to isolate the affected device.
While these actions are being carried out, the SOAR would automatically gather forensic evidence, including email headers, user activity logs, and network flow data, storing them centrally for analysis and documentation. Notifications to stakeholders would be sent automatically through pre-integrated communication tools like Slack or Microsoft Teams, and a detailed incident ticket would be created in the IT service management system to track remediation progress. Analysts could be asked for confirmation at certain steps, simply making sure the actions may be carried out.
The difference is significant. Without SOAR, the analyst would spend hours juggling tools, manually executing tasks, and documenting their efforts, leading to delays and potential gaps in the response. With SOAR, all repetitive and time-consuming steps are automated, reducing the response time from hours to minutes. At the same time, the SOAR ensures every action is documented, making post-incident reporting and compliance straightforward. This allows analysts to focus on strategic aspects of the incident, such as understanding the broader implications or improving defenses to prevent future attacks.
SIEM vs. SOAR: A Detailed Comparison
Both SIEM and SOAR collect information from various devices and data sources, enriching it with threat intelligence and other contextual information to support decision-making. However, their similarities end there. SIEM and SOAR play distinct roles within the SOC.
The following table provides a clear overview of the differences and complementary roles of SIEM and SOAR:
| Aspect | SIEM | SOAR |
|---|---|---|
| Primary Purpose | Log centralization, threat analysis, and detection | Incident response management and automation |
| Main Function | Collects, correlates, and analyzes logs to identify threats | Orchestrates and automates security incident responses |
| Data Type | Event logs, historical and real-time data from multiple sources | Enriched incident data and response playbooks |
| Capabilities | Real-time detection, event analysis, historical investigation | Task automation, playbook execution, tool coordination |
| Data Enrichment | Yes, with threat intelligence integration and external data sources lookup, to help detect potential threats. | Yes, with threat intelligence integration and external data sources lookup, focused on incident data to aggregate context to a detection. |
| Automation | Limited; primarily focused on analysis and alerts | High; automates repetitive tasks and workflows |
| Primary Benefit | Comprehensive visibility and threat detection | Fast, efficient incident response with reduced manual workload |
| SOC Maturity Level Needed | Basic to intermediate; useful for detecting and analyzing threats | High; typically requires visibility foundation (often provided by SIEM) |
| Compliance and Auditing | Helps meet regulatory requirements with centralized log storage | Not the primary focus but can assist in compliance automation |
| Role in SOC | Threat monitoring and detection, compliance support | Automated incident response, workflow optimization |
| Recommended Implementation | First layer of defense, essential for detection and compliance | Best as an additional layer for response automation following SIEM |
Which Tool is Better for Your Organization?
Both tools offer significant benefits, the ideal choice depends on your organization’s security needs and maturity level.
SIEM provides critical visibility into the security environment, allowing you to detect threats, identify security gaps, and strengthen your infrastructure. For many organizations, SIEM is also essential for compliance as it serves as a centralized record of all activity, providing an evidence trail for audits and regulatory requirements.
SOAR generally requires a mature security infrastructure and is most effective when layered on top of a SIEM. Once SIEM provides the foundational visibility, SOAR’s automation capabilities help elevate security response to the next level, enabling efficient and organized incident response across multiple systems.
While SIEM offers robust detection and insights, SOAR is designed to make security operations faster and more efficient through automation. For many organizations, a complementary approach, starting with SIEM for detection and then integrating SOAR for response automation, creates a powerful and scalable security solution.
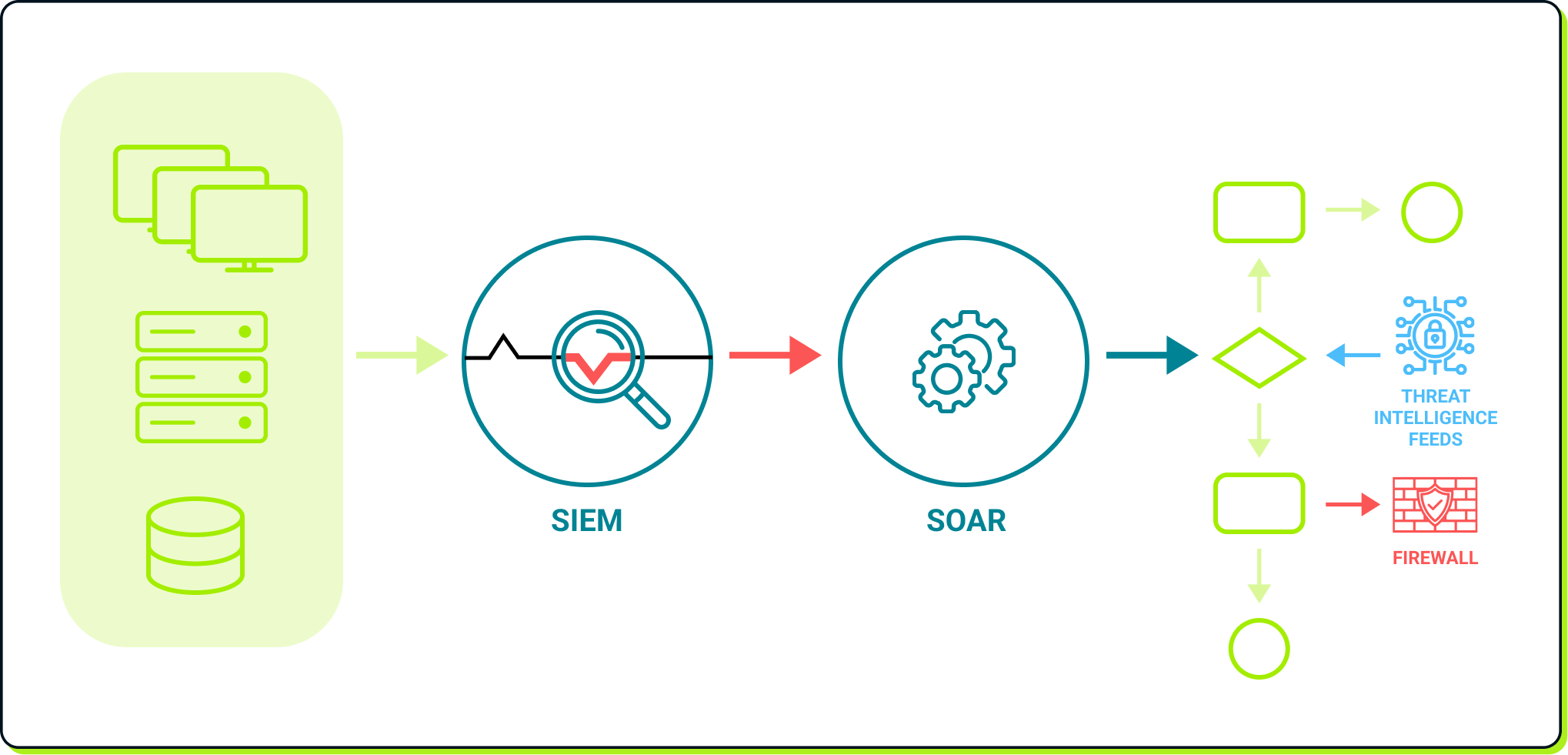
In this updated scenario, devices forward their logs to the SIEM, which centralizes detection through correlation and intelligence, improving detection accuracy. When a threat is identified, the SOAR is alerted and initiates playbooks to triage and mitigate the incident effectively.
This approach enables the SIEM to analyze data centrally, enhancing detection accuracy, while passing its findings to the SOAR for automated responses. Together, this synergy greatly enhances the efficiency of the SOC.
Choosing the Right SOC Tools for Your Organization
To select the most effective SOC tools, assess your SOC’s current maturity level and define your immediate goals. If your team has advanced automation skills, in-depth network knowledge and there are already tools detecting threats, implementing a SOAR platform can optimize and enhance SOC operations, making them more organized and action-driven. Still, implementing a SOAR without a SIEM will be a challenging task. On the other hand, if you manage a large infrastructure with limited visibility, with low or zero detection capabilities, a SIEM can provide the comprehensive insights needed to monitor and understand your environment.
For a fully operational SOC, the combination of SIEM and SOAR is ideal. These tools complement each other, delivering a comprehensive approach to security monitoring, automation, and response. Together, they provide the visibility, intelligence, and automation necessary to stay ahead of threats in a complex and evolving security landscape.
Other Essential SOC Products
While SIEM and SOAR form the core of many SOCs, additional tools can enhance security operations and address specific needs:
- Endpoint Detection and Response (EDR): Monitors and analyzes endpoint activity to detect, investigate, and respond to threats. EDR solutions enable SOC teams to isolate compromised devices and contain threats at individual endpoints.
- Cloud Detection and Response (CDR): As an emerging technology, CDR enables SOCs to detect, investigate, and respond to cloud-specific threats, such as misconfigurations and unauthorized access. CDR provides real-time visibility across multi-cloud environments, using behavioral analytics to identify anomalies.
- Threat Intelligence Platforms: Aggregate and analyze threat intelligence data to provide insights into known threats, attack patterns, and indicators of compromise (IOCs). These platforms help SOC teams stay updated on the latest threats and proactively detect potential attacks.
Final Recommendations
For organizations considering SIEM, SOAR, or both, it’s essential to evaluate current security needs, resources, and maturity level:
- Start with SIEM if your organization needs centralized visibility and threat detection capabilities. SIEM serves as the foundation for security operations, offering insights that are critical for identifying potential vulnerabilities and ensuring regulatory compliance. For organizations with limited automation capabilities, SIEM alone can still significantly enhance detection and monitoring.
- Implement SOAR when your SOC has matured and requires efficient, scalable response processes. SOAR builds on the foundation provided by SIEM, making incident response more efficient by automating repetitive tasks and orchestrating responses across multiple tools. SOAR is ideal when your SOC is handling a high volume of alerts and requires faster, standardized responses.
Combined, SIEM and SOAR will result in an optimized, fully operational SOC. This dual approach offers both visibility and automated response, creating a holistic solution that empowers SOC teams to detect, investigate, and resolve threats quickly. Organizations with complex environments or high regulatory requirements will benefit from this comprehensive setup, as it allows them to handle incidents more effectively and at scale.








