In today’s fast-paced digital landscape, organizations are increasingly adopting cloud services, remote work, and mobile connectivity to stay competitive and agile. This shift brings about new challenges for network security and performance, as traditional security models struggle to keep pace with the demands of modern, distributed environments.
Enter secure access service edge (SASE), a transformative approach that combines networking and security into a unified, cloud-native service. SASE not only simplifies network architecture but also enhances security, scalability, and user experience.
In this blog post, we will delve into the fundamentals of SASE, exploring its key components and how they collectively address the pressing security challenges of the digital era. From zero trust network access (ZTNA) to cloud access security brokers (CASB), we will uncover how SASE revolutionizes the way organizations secure their networks and empower their workforces.
What is secure access service edge (SASE)
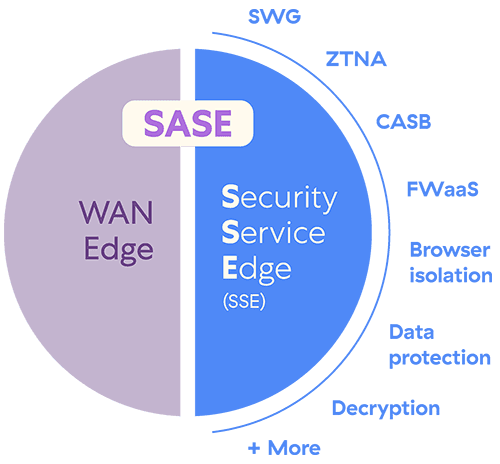
SASE is a term coined by the Gartner organization, it combines two key technologies: SD-WAN for network connectivity and SSE (security service edge) for security, forming a unified, cloud-delivered service model. It integrates services such as a secure web gateway, firewall, and zero trust network access into a single cloud-native solution. SASE ensures secure and efficient access to websites, applications and data from any location. This unified approach simplifies network management, enhances security, and improves user experience by dynamically adapting to the needs of a modern, distributed workforce.
Services that build SASE
Software-defined wide area networking
SD-WAN is a technology that optimizes and simplifies the management of a wide area network by decoupling the network hardware from its control functions. It enables enterprises to securely connect users to applications by leveraging a combination of different transport services, including MPLS, LTE, and broadband internet.
SD-WAN enhances network performance and reliability by dynamically routing traffic based on current network conditions, application requirements, and security policies. This results in improved application performance, reduced operational costs, and increased agility, making it an ideal solution for businesses embracing cloud services, remote work, and digital transformation initiatives. It provides a single pane of glass for the whole network.
Secure internet gateway
SIG can be seen as a precursor of SSE. Initially, SIGs were designed to secure internet-bound traffic by secure web gateway (SWG) capabilities. As organizations started adopting cloud services and remote work models, the limitations of traditional SIGs became noticeable. In response to these new challenges, SIG evolved to SSE, expanding security features by incorporating additional security services such as cloud access security broker (CASB), zero trust network access (ZTNA), and comprehensive data loss prevention (DLP). Nowadays, the term SIG is rarely used and has been replaced by SSE.
Security service edge
In recent years, the application development model has evolved, resulting in data being distributed across various locations. Companies now store their information on-premises, in public or private clouds, or directly within SaaS applications. Additionally, users have changed their working habits. Instead of being confined to the office, they now work from remote locations on flexible schedules. As a result of those changes, security products have had to adapt accordingly.
SSE is a cybersecurity framework that integrates multiple services into a unified, cloud-delivered solution designed to protect users, applications, and data regardless of their location. SSE incorporates key security functions such as zero trust network access (ZTNA), cloud access security broker (CASB), and secure web gateway (SWG), enabling secure access to the internet and cloud-based applications. It can also protect remote users and IoT devices.
By centralizing and simplifying security management, SSE helps organizations enforce consistent security policies, improve threat detection, and ensure compliance with regulatory requirements, all while supporting the dynamic needs of a modern, distributed workforce. Enterprises do not have to use their local network to route traffic to the main firewall in the data center, instead all locations can connect to the SSE cloud and send traffic directly to it, so the overall latency for the traffic is lower. The data in transit is protected by VPN tunnels that encrypt all packets before sending them to the public network.
To delve more deeply into this topic, let’s focus a bit more on SSE.
Components of SSE
Zero trust network access
ZTNA is a modern security framework that represents the principle of "never trust, always verify". Unlike traditional security models that grant broad network access once a user is authenticated, ZTNA continuously verifies every request, regardless of where it originates. It provides granular, secure access to applications and data based on user identity, device health, and other contextual factors, ensuring that only authenticated and authorized users can access specific resources. Trust is not assumed by default, everything is blocked at the beginning, and specific applications or traffic types must be permitted. ZTNA provides a scalable and adaptable method for protecting organizational assets, establishing itself as an essential element of contemporary cybersecurity strategies. This solution enables the company to identify who is accessing its data and where it is stored, offering centralized visibility and control over the data.
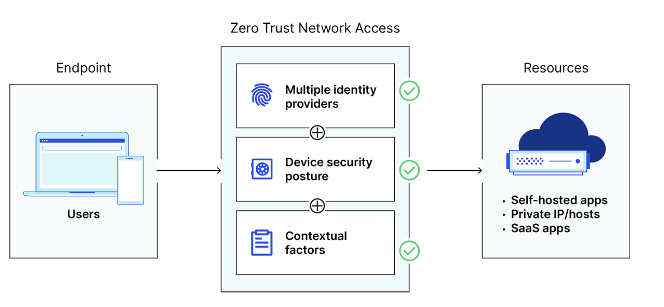
ZTNA uses multi-factor authentication (MFA) for user authentication, followed by verification of the device's security posture against the organization's standards, such as updated antivirus software and enabled encryption. Following successful authentication, the user is granted access exclusively to resources and applications defined by policies; any other type of traffic is blocked.
The most popular solutions include Cisco Secure Access by DUO, Zscaler Private Access, and Prisma Access by Palo Alto, among others.
Secure web gateway
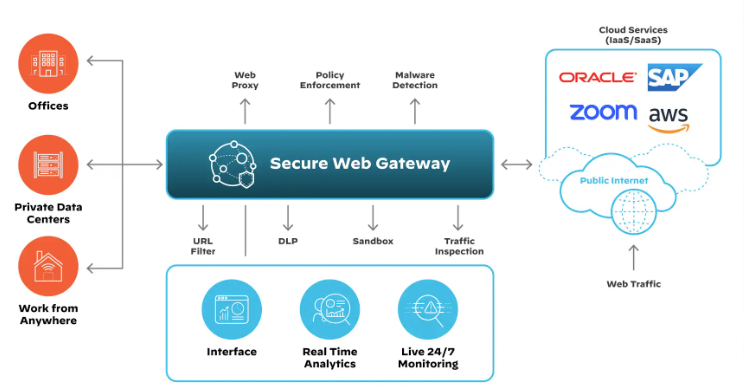
SWG is a crucial component that protects organizations from web-based threats and enforces web access policies. As part of the SSE framework, SWG provides secure and controlled access to the internet by filtering and inspecting all web traffic for malicious content, such as malware, viruses, phishing attempts, and other cyber threats. It enforces organizational policies by blocking access to inappropriate or risky websites and applications, ensuring compliance with regulatory requirements.
SWG benefits from centralized management and visibility, allowing security teams to apply consistent security policies across all users and devices, regardless of their location. By decrypting and inspecting SSL/TLS traffic, SWG detects and mitigates threats that might otherwise be hidden in encrypted web sessions. The solution can be integrated with SIEM solutions and notify administrators of any problems or security concerns.
This comprehensive web security approach enhances the overall security posture of the organization, ensuring that users can safely and efficiently access the internet and cloud-based applications while maintaining protection against emerging threats.
Popular solutions include Cisco Umbrella, Symantec Web Security, and Zscaler Internet Access.
Cloud access security broker
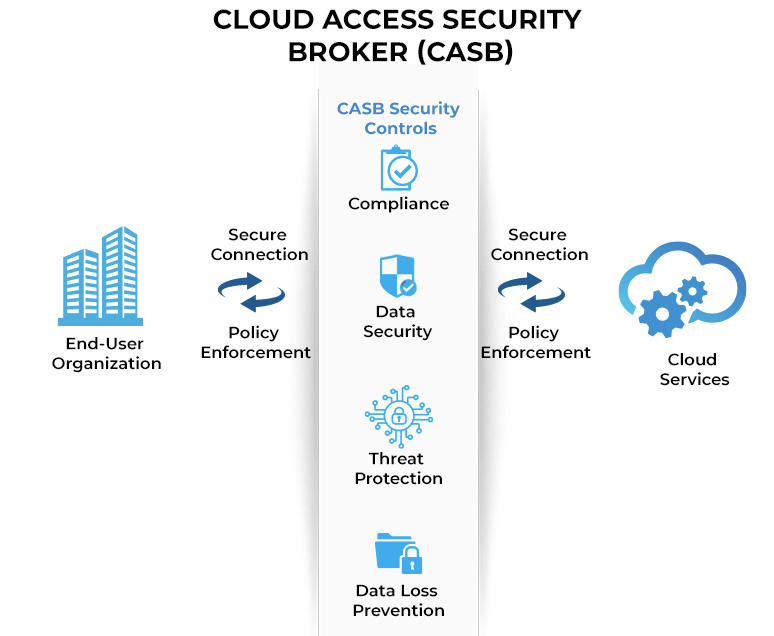
CASB is a security solution that acts as a control point between cloud service users and cloud applications, providing visibility, compliance, data security, and threat protection. CASBs enforce security policies for cloud-based resources, ensuring that data stored in and accessed from cloud services is protected from unauthorized access and threats. They offer capabilities such as data loss prevention (DLP), user activity monitoring, and real-time threat detection to secure sensitive information and maintain regulatory compliance. By delivering comprehensive security controls and granular visibility into cloud usage, CASBs help organizations safely embrace cloud services while mitigating associated risks. It tracks user activity and provides detailed logs and reports, so even if a security breach occurs, it is possible to investigate the incident.
Leading solutions include Microsoft Defender for Cloud Apps, Palo Alto Networks Prisma Access, and Symantec Cloud SOC.
Firewall as a service
FWaaS is a vital component that provides advanced firewall capabilities through a cloud-delivered model. While SWG primarily protects web traffic, FWaaS can do much more - it can support other protocols like SIP, FTP or DNS.
This solution extends next-generation firewall functions, such as traffic filtering, threat detection, and intrusion prevention, to the cloud, enabling consistent and scalable security enforcement across distributed environments. By integrating FWaaS within the SSE framework, organizations can benefit from centralized management, ensuring that security policies are uniformly applied regardless of user location or device. FWaaS in SSE protects against network threats by inspecting and filtering traffic based on predefined security rules and real-time threat intelligence. It helps secure internet-bound traffic, internal communications, and access to cloud applications, contributing to a holistic security posture.
This approach not only simplifies firewall management but also enhances flexibility and scalability, making it easier for organizations to adapt to changing security needs in an increasingly mobile and cloud-centric world. It also allows organizations to focus on their business goals instead of on-site firewall deployment and maintenance.
Top choices include Zscaler Internet Access, Perimeter81, and Cisco Secure Firewall among others.
Security challenges and SASE solutions in a remote world
Secure access service edge can be a solution to many challenges in today’s remote business environment. Below, we list the most common issues and possible SASE measures organizations can take to overcome them.
Complexity and fragmentation of security solutions
Challenge: Traditional network architectures often engage multiple, disjointed security solutions from various vendors, which leads to complexity and difficulties in management.
SASE Solution: SASE unifies networking and security functions into a single, cloud-native service, simplifying management and reducing the need for multiple point solutions.
Secure remote access
Challenge: With the rise of remote working, ensuring secure access to corporate resources from various locations and devices has become critical. Traditional VPN solution has number of limitations:
- Security risks: A VPN takes a perimeter-based approach providing access to the entire network once trusted, leaving other security concerns to be taken care of by firewalls and other security measures.
- Scalability issues: A VPN can struggle to scale efficiently with a large number of remote users, leading to performance bottlenecks.
- User experience: VPNs can degrade user experience due to latency and bandwidth limitations caused by limited bandwidth capacity, geographical distance, centralized architecture, encryption overhead and other security measures, like firewalls, that traffic needs to pass.
- Limited monitoring: Visibility into user activities and potential threats is limited to the knowledge that a user has accessed the network. It's hard or impossible to verify what applications or resources have been accessed and how long they have been used.
SASE Solution: SASE provides secure, scalable remote access through integrated ZTNA, offering granular access control, continuous verification, elastic scaling due to its cloud-based nature and low-latency access thanks to a global network of points of presence.
Protection of cloud and SaaS applications
Challenge: Traditional security architectures struggle to effectively secure access to cloud and software as a service (SaaS) applications. There are several challenges, including:
- Limited visibility and control: Typically it's hard to ensure comprehensive visibility and control over cloud and SaaS applications access and usage. It can result in shadow IT, where users use unsanctioned cloud services which can lead to data breaches, or regulatory violations (like GDPR or HIPAA).
- Inconsistent security policies: Security policies are often fragmented across different environments, leading to inconsistent enforcement and potential security gaps.
- Threat detection: Traditional security solutions usually rely on signature-based methods, which can only detect known threats. They are ineffective against unknown or zero-day malwares and vulnerabilities.
- Performance and scalability issues: Usually traffic is routed through a central data center for inspection which increases latency, degrading user experience and making it difficult and costly to scale.
SASE Solution: SASE includes cloud access security broker (CASB) and secure web gateway (SWG) functionalities to secure access to cloud applications, enforce security policies, and monitor user activity in real-time. SASE employs distributed architecture with global points of presence to resolve performance issues, behavioral analysis and machine learning to improve threat detection, and its cloud-based nature makes this solution scalable.
Network performance and reliability
Challenge: Ensuring optimal network performance and reliability, especially for geographically dispersed users and applications, can be difficult.
SASE Solution: SASE optimizes network traffic using a global network of POPs and its integrated WAN capabilities, improving performance and reliability through techniques like WAN optimization and SD-WAN.
Consistent security policies across the network
Challenge: Maintaining consistent security policies across different network environments (on-premises, cloud, remote) is challenging.
SASE Solution: SASE enables centralized policy management, allowing organizations to enforce consistent security policies across all users, devices, and locations.
Scalability
Challenge: Traditional network security solutions may not scale efficiently with the growing number of users, devices, and applications.
SASE Solution: As a cloud-native solution, SASE can easily scale to accommodate increasing demands without the need for significant hardware investments.
Threat protection and detection
Challenge: Effective threat protection and real-time threat detection are essential for modern network security.
SASE Solution: SASE consolidates multiple security functions, such as secure web gateway (SWG), cloud access security broker (CASB), zero trust network access (ZTNA), and data loss prevention (DLP), into a single, integrated platform implementing advanced threat detection capabilities like behavioral analysis and real-time threat intelligence.
Simplified compliance
Challenge: Complying with various regulatory requirements and standards can be complex and resource-intensive.
SASE Solution: SASE helps organizations simplify compliance by providing comprehensive security controls and centralized logging and reporting, making it easier to demonstrate compliance with regulatory requirements.
Possible use cases of SASE
Branch office security
If an enterprise already has a working network that connects its headquarters and branch offices together, SSE might serve as a comprehensive security solution for the entire system. By combining SSE and SD-WAN, an enterprise can achieve a complete SASE model, where it can use application-aware routing delivered by SD-WAN and security features from SSE stack.
Each branch can leverage its existing internet connections to connect to the SSE cloud, allowing traffic to be sent securely and directly to the internet without backhauling traffic to the central data center for inspection using WAN links. This scenario reduces the load on the local network while still providing security protection for each branch. Additionally, SSE enables consistent security policies across all locations, ensuring that each branch follows the same standards and protocols.
Remote users protection
As remote work becomes increasingly prevalent, ensuring the security of remote users has become a critical concern for enterprises. SSE offers a comprehensive solution that integrates multiple security services to protect remote users regardless of their location. In a standard model, all users connect to a VPN concentrator that needs to handle hundreds if not thousands of connections and all the traffic that is generated by the users. Also, once the user is connected, it can access all resources without any further verification.
Enterprises can reduce bottlenecks by redirecting their traffic directly to the internet, without sending it first to a headquarters or data center for inspection via a firewall. SSE can monitor and filter internet-bound traffic from remote users, ensuring protection against web-based threats. Additionally, it secures traffic to cloud services and internal applications by employing zero trust principles, which involve continuous verification of user identity and device health before granting access.
An administrator can monitor and track all remote devices from a single pane of glass, ensuring they are using the latest software versions and blocking connections from devices that do not comply with all restrictions.
Securing SaaS applications
Ensuring the security of SaaS applications is essential to protect sensitive data and maintain compliance with regulatory standards. Utilizing tools such as cloud access security brokers (CASBs), organizations can gain visibility into application usage, enforce security policies, and prevent data breaches. Additionally, implementing strong identity and access management (IAM) controls, such as multi-factor authentication (MFA), helps verify user identities and restrict unauthorized access. By adopting these measures, enterprises can safeguard their SaaS environments against cyber threats and ensure that only authorized users can access their applications and data.
Summary
In the world of remote work and cloud services, traditional network security models face significant challenges. Secure access service edge (SASE) emerges as a modern solution, converging network and security functions into a single, cloud-native service. SASE integrates key technologies such as secure web gateway (SWG), cloud access security broker (CASB), zero trust network access (ZTNA), and firewall as a service (FWaaS), providing comprehensive protection for users, applications, and data, regardless of location. By simplifying network management and enhancing security, SASE addresses the evolving needs of businesses, offering a scalable and efficient approach to securing digital transformation initiatives.








