VM, VDI, VIM, NFVI, VLAN, VXLAN, VNF - the famous ‘V’ that dominates today’s IT world stands, of course, for ‘Virtual’. Every day we use virtualized servers, storage, desktop or networks without even realizing it. The convenience, cost-saving, enhanced features and security are just some of the reasons why we start using virtualization and often never look back.
The same is true for computer networking, where a single physical network can host multiple separated, logical (virtual) networks that may have different topologies and feature sets or even carry traffic of different customers without interfering with each other.
There are multiple protocols and approaches to creating a virtual network, among which we can find the VLANs (Virtual Local Area Network) and VXLANs (Virtual eXtensible Local Area Network). The names of the protocols already suggest that there are some similarities between them, so let’s get into the details.
VLANs and VLAN ID
VLAN is an extension to the Ethernet protocol, which adds the 802.1Q header to the Ethernet frame. This extra header gives networking devices the ability to tag traffic with a number from 1 to 4094 (called VLAN ID), where each possible number signifies a different virtual network.
Computers and servers connected to a specific, single VLAN will only ever see frames that belong to the same VLAN, as they effectively belong to a network that is separate from other virtual or physical segments.
VLAN header also adds QoS marking capabilities to Ethernet packets, but we will concentrate on network segmentation in this article.
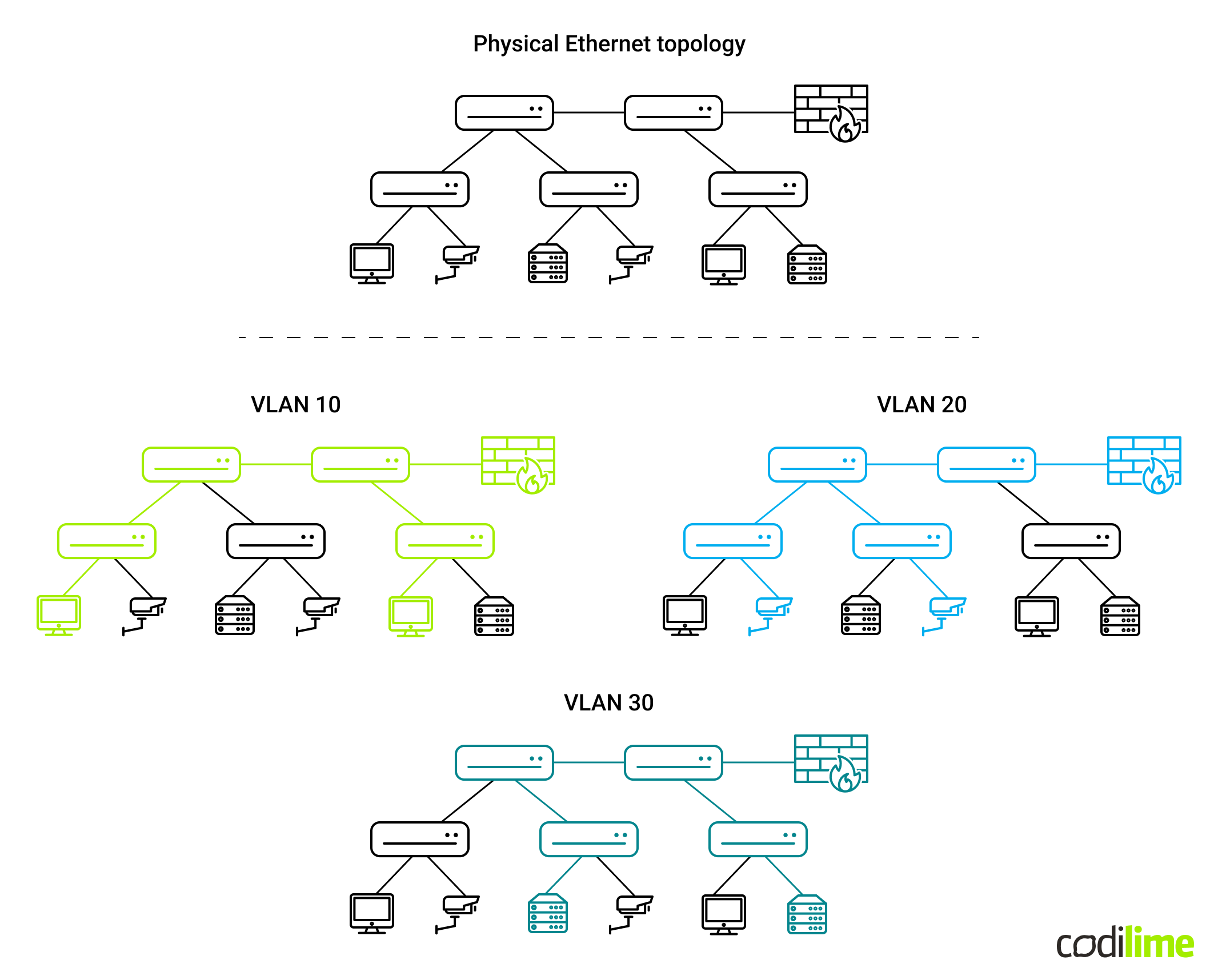
This has been visualized on a simple diagram above, where there is a single physical network underlay consisting of five switches, a firewall and multiple end devices. The switches have been configured in such a way that PCs belong to VLAN 10, IP Cameras belong to VLAN 20, and servers belong to VLAN 30, which gives us three logical networks that are securely separated from each other, even though they use the same physical network infrastructure. The only way they can communicate is over the firewall, which is connected to all three VLANs and can forward traffic between them.
The support for VLANs on networking devices is very widely available, even on inexpensive platforms, and this method of network virtualization is commonly used in most small-business and enterprise networks.
The VLANs are easy to configure in small networks, but the maintenance can actually become problematic in the case of larger environments, where issues with redundancy, loop avoidance and large broadcast domains require extra care.
VXLANs and VXLAN Network Identifier
VXLAN is a tunneling protocol that encapsulates Ethernet frames inside UDP packets. This means that VXLAN does not care what the underlay physical network topology is - as long as it can carry UDP packets, it can be used to provide Ethernet (Layer 2) connectivity between remote network segments.
Similarly to VLANs, the VXLAN header makes it possible to tag the traffic with a specific number that determines to which virtual network the packet belongs. This number is called VNI (VXLAN network identifier), and it can have over 16 million unique values.
By properly configuring switches, routers and other entities such as hypervisors, we can assign specific end hosts (servers, virtual machines, firewall interfaces, etc.) to specific virtual networks, thus building new overlay network topologies. An example of that has been shown on the topology below, where tunnels carrying VNI 1000 and VNI 1001 create separate networks. The only way to communicate between these logical networks is through the IPS device, which is connected to both.
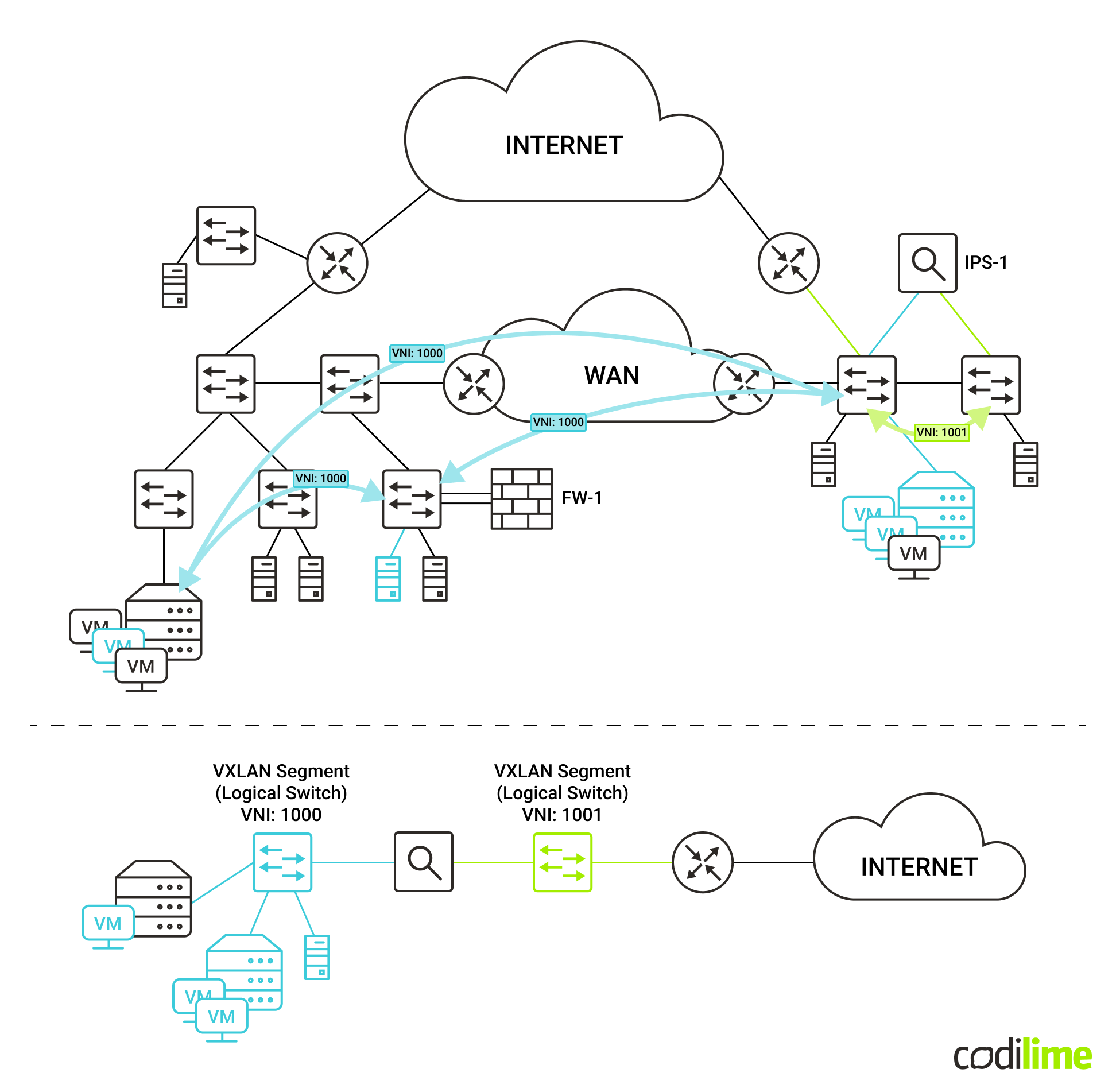
While the use of VXLAN tunnels started in Data Center environments, it has become more common in Enterprise networks as well. It allows building a topology where connections between networking devices are Layer 3, with the dynamic routing protocol such as OSPF taking care of redundancy, fault detection and loop avoidance. The Layer 2 connectivity over such a Layer 3 network, whenever needed, is provided by the use of VXLAN tunnels.
If so, why are we all not using VXLANs in our networks already?
The networking devices that support it, while relatively common, are usually significantly more expensive. Also, properly configuring VXLAN tunnels requires a lot of manual work or the use of an often complicated tool that can do the job in an automated fashion. A popular approach is to use BGP EVPN, but this extends the requirements for protocols that underlying network devices must support.
If you encounter any network issues while setting up VLAN or VXLAN, you may need to perform some network troubleshooting. This guide on network troubleshooting Linux can help you diagnose and resolve issues related to your Linux network configuration.
Main differences between VLAN and VXLAN
Having a general idea of how VLANs and VXLANs work, let’s compare their main characteristics side-by-side.
Criteria | VLAN | VXLAN |
Encapsulation | Ethernet frame with 802.1Q header | VXLAN header carried by UDP datagram |
Underlay requirements | Layer 2 Ethernet connectivity to all endpoints that need to make use of VLANs | Layer 3 connectivity between each VXLAN tunnel endpoint |
Redundancy and loop avoidance | Limited to Ethernet-based solutions, such as Spanning Tree Protocol, TRILL, SPB, MC-LAG, switch fabrics | Whatever is supported by Layer 2 and/or Layer 3. |
Scalability | Limited: - large Ethernet segments are not recommended | Very high: - over 16 million virtual networks - pure Layer 3 networks with BGP can be extremely large and with complex topologies - can be extended to wherever the Layer 3 connectivity reaches |
Ease of configuration and maintenance | Simple in small networks. Requires extra care and can get troublesome in large environments.
| Manual configuration is complex, even in small networks. Can use multicast, BGP or proprietary solutions such as SDN controllers as a control plane that automatically establishes required VXLAN tunnels. |
Flexibility | Low: - optimal use of available network paths requires extensive use of Ethernet link aggregation, which often requires the use of a proprietary mechanism such as MC-LAG - can be tunneled only by Layer 2 tunneling protocols | High: - virtual topologies are not limited by the underlying physical network - the traffic can be forced using VXLAN tunnels through multiple devices before reaching its destination (so-called Service Chaining) - can be tunneled in other Layer 2 or Layer 3 tunneling protocols |
Equipement cost | Low | Medium/High |
Extra caveats | Requires MTU larger than the standard 1500 bytes. Otherwise, VXLAN datagrams may require fragmentation which is not always possible. Lower throughput on a single link due to bigger header overhead when compared to Ethernet VLANs. |
As you can see, for mechanisms that serve the same purpose, there are quite a few differences between VLANs and VXLANs. But is one better than the other?
As with all things, it depends on the problems we are trying to solve.
If the goal is to separate printer, CCTV and user traffic in a small office, then VLANs will get the job done quickly and easily without the need to deal with the complexities of BGP or SDN controllers. On the other hand, if the goal is to provide connectivity between servers, VMs, and other entities in a large, multi-tenant data center, then choosing VXLAN over VLAN is the only sane solution.
If you want to learn more about networks, check out our other articles:
- How to configure VNFs using a Virtual Network Function Descriptor
- Example use case of network troubleshooting during the VNF lifecycle
- Network traffic troubleshooting during VNF lifecycle - aspects of Tungsten Fabric flows
Conclusion
Network virtualization is present in one way or another in most modern computer networks. The easy-to-use VLANs are commonly encountered as VLAN technology has widespread support in software and hardware. The VXLANs are the newer alternative, which is already prevalent in large data center environments and gains ground in enterprise networks as well. However, there is little chance that VXLANs will completely phase out the use of VLANs, as they remain a fine and inexpensive choice in less complex and less dynamic networks.








